CrowdStrike fal.con 2024
We were lucky enough to attend the CrowdStrike conference, Fal.con, this past week in Las Vegas. With CrowdStrike’s growing number of modules and products, there are too many updates to cover. However, in this blog we will try to distill some of the more notable takeaways and give our take on their impact to CrowdStrike customers.
Disclaimer: This blog includes our opinions and impressions from the CrowdStrike conference. Please refer to CrowdStrike’s public announcements for authoritative detail on any product features.
Don’t Call It A Comeback
After a summer of Falcon related Windows BSODs, CrowdStrike went all out for Fal.con 2024 in an attempt to rehab customer relationships and define a blazing trail of innovation for the future of security. Between the happy hours and the Tiësto fueled Fal.con Fest, a lot of interesting information came out of the conference. In general, we continue to be impressed with the velocity of innovation and development that has become a hallmark of CrowdStrike over the years. It’s clear that they are pushing the entire industry to take things to the next level in regard to unified security platforms. With the recent additions of Next-gen SIEM, expanded exposure management functions, and AI innovations along with its industry-leading EDR, CrowdStrike is getting us closer and closer to that single-pane of glass that security professionals have been dreaming about for decades. While there were some exciting new announcements there are still areas of the platform where the jury is still out. Below we will outline some of the new or “coming soon” features which we are tracking to see what value they may bring our customers.
Next-gen SIEM
One of the most exciting products for us here at Helios is CrowdStrike’s introduction of NG-SIEM. Most security teams have had a love/hate relationship with SIEMs since their inception. While they can be extremely powerful investigation tools and a must-have part of your security stack, SIEM management can be very burdensome including keeping log sources properly parsed/healthy, mastering complicated query syntax, and SIEM application upgrades. The other challenge with SIEMs is that sometimes it is not feasible to bring in enough of that juicy data due to ingestion limits or otherwise unwieldy sources. Over the years, EDR has taken center stage when it comes to most investigations due to the plethora of endpoint data they provide in an easily searchable UI. In a perfect world, you would bring all your EDR data into your SIEM to have all of your logs in one place. However, due to the aforementioned limitations, this is not feasible for most organizations working with a limited budget.
CrowdStrike (and others) has turned the SIEM model on its head. Instead of bringing the EDR data to the SIEM, they have brought the SIEM to the EDR data. This has created a common storage location and query language for not only your EDR data, but also all those 3rd party logs like your firewall, email security, and authentication source. This unified approach is a force multiplier for security analysts and detection engineers as the data is now easily correlated in the same tool.
What’s New in NG-SIEM
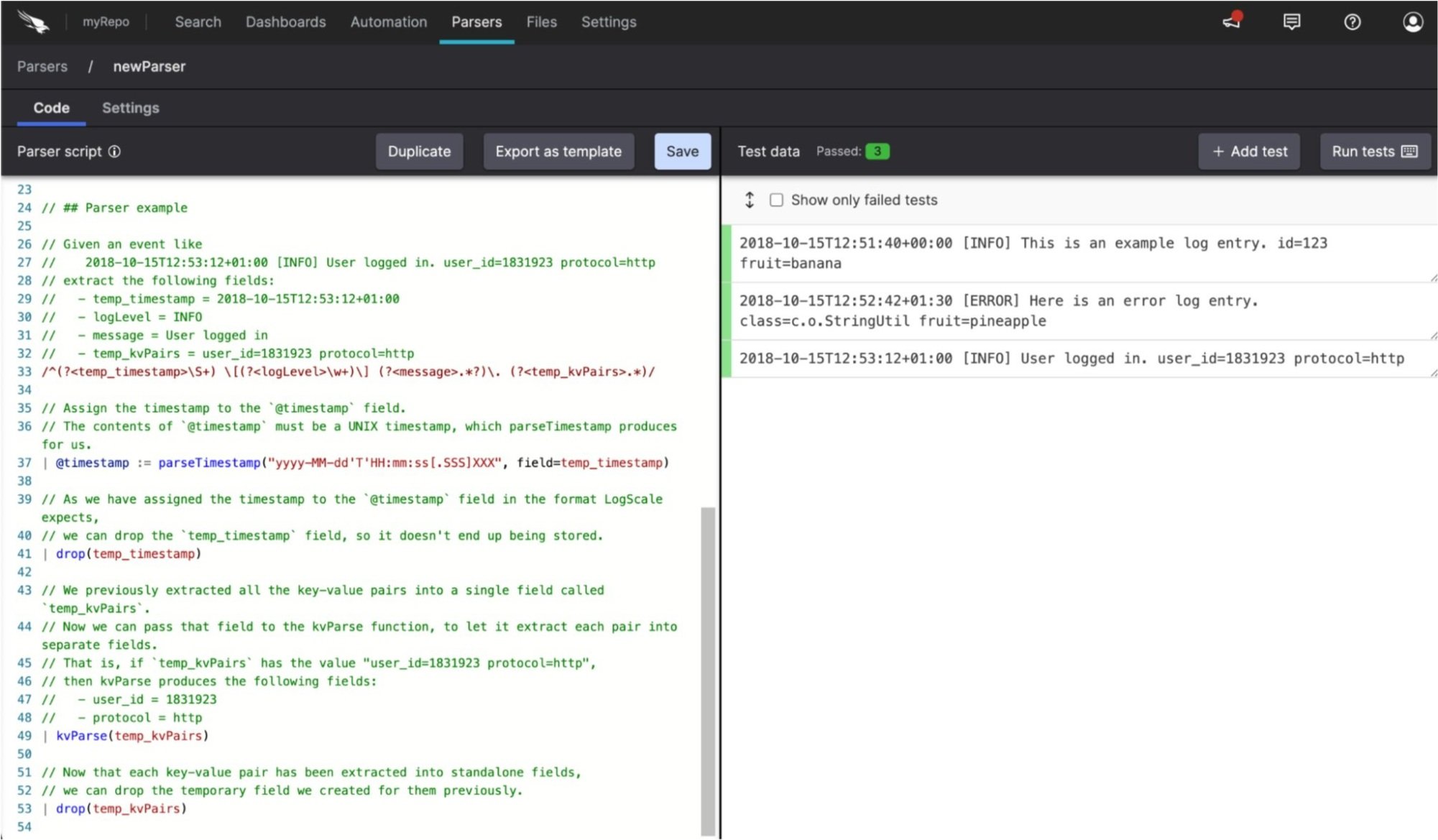
The rapid evolution of CrowdStrike’s NG-SIEM continues with several new features that are either being released or are on the short-term roadmap. While not exactly a new feature, one of the most impactful announcements is CrowdStrike’s commitment to double-down on producing new, managed data parsers for a wider array of data sources. Data parsers are the mechanism in which a SIEM uses to extract raw log source data and make it searchable based on field for an analyst. For example, you could not search ‘SrcIP=8.8.8.8’ without the network flow data being parsed.
CrowdStrike reports their goal is to churn out 30-40 new data parsers per month while also maintaining the currently supported parsers. Furthermore, they are working with their tech alliance partners to create their own CrowdStrike parsers for their products. This is a huge win for weary technologists who have been dealing with creating complicated, custom parsers for all their data sources. While there will always be a need to create and maintain custom or in-house parsers, CrowdStrike’s commitment to take this on inspires our continued confidence in the platform. CrowdStrike is also purporting to be able to introduce AI that will lend a hand in creating custom parsers. See the AI innovations section later in the blog for details.
NG-SIEM Parser Snippet
Another new feature which CrowdStrike announced is what they are calling Detection Posture Management. In short, NG-SIEM will map all of your built-in detection logic to the MITRE ATT&CK framework to give your teams visibility of what tactics and techniques you may have coverage. The mapping not only includes the detection logic built into your EDR and CrowdStrike 1st-party products, but is also purported to include the correlation detection logic which is covered by 3rd party data ingestion and integrations. It is also possible to filter down to controls that may be leveraged by a specific threat actor such as Scattered Spider. The idea is to give a holistic view of what controls you have in place to address each of the MITRE techniques.
While we believe that this is a nice added feature, we do have concerns that this will lull IT teams into a false sense of security. Keep in mind that coverage of each MITRE technique is not usually a binary. There is a lot of nuance to how strong your controls are around a particular technique (e.g. details of the technique, is it covered in all parts of your environment, on-prem vs cloud, endpoint vs application, etc). While this feature can be a minimum bar to grade your security posture and something you can add to your executive team’s slide deck, keep in mind that this may create a false picture of reality.
There were several other quality of life items which CrowdStrike teased in its roadmaps for NG-SIEM including further maturing its query language with things like field aliasing and temp table creation for easier data joins. Furthermore CrowdStrike announced a new NG-SIEM connector for Cribl, allowing easy ingestion from the popular data engine. Overall, there weren’t any announcements that we consider game changers but that is not what we would expect from a maturing product that is still trying to catch up to feature parity with other dedicated SIEM companies. The pledged commitment to expanding integrations and OOTB parsing alone was more than we needed to hear to know that this product is a good investment for anyone already in the CrowdStrike platform who is either looking to start their SIEM journey or wants to leave their old SIEM behind to consolidate tech stacks.
Exposure Management
Exposure Management is CrowdStrike’s rebranded and expanded vulnerability management module. CrowdStrike entered the VM space with ‘Spotlight’ a few years ago to help organizations who were already in the CrowdStrike universe and needed some basic vulnerability identification capability. Spotlight has grown in depth and maturity quite a bit since its initial release and has become a solid tool to identify vulnerabilities on Falcon managed endpoints. Spotlight still has some limitations (e.g. vendor and CVE coverage) and in no way stacks up to the VM tools touted by some of the mature players in the space (e.g. Tenable), but nonetheless it is hard to argue with its convenience since vulnerability assessments run automatically through the Falcon agent on managed hosts.
What’s new in Exposure Management
It has been teased for a long time but CrowdStrike again signaled that they are going to be allowing network vulnerability scanning from their CrowdStrike agent. In theory, you could leverage any CrowdStrike agent to scan the local network and identify vulnerabilities. However, the details provided were a little…sparse, if not guarded. We only saw screenshots of what this feature may look like. There was no mention of whether these could be credentialed scans or simply blind scanning on the local network. It seems that their short-term goal is to target vulnerabilities on local networking devices but again, little detail was given about the mechanisms or detection completeness. Overall, we were underwhelmed as this is a feature we have been excited about. We believe this feature has a lot of potential but it was clear to us that it in no way will replace your dedicated network vulnerability scanner any time soon.
There were some other Exposure Management roadmap features which we did think were really promising. CrowdStrike demoed their browser extension risk inventory which could be a big win for teams who allow users to autonomously install extensions. CrowdStrike’s browser extension module allows you to inventory all browser extensions used in your organization and rank them by risk based on the permissions which they have in the browser (guessing similar to CRXcavator).
CrowdStrike also flexed their CIS benchmarking capability which we were very impressed with. The feature allows you to CIS benchmark your hosts directly through the Falcon agent. A couple things that excited us about this is the fact that you could easily modify the expected values in the UI for the benchmark. For instance, if your organization requires 12-character passwords instead of 8, you can modify the expected value from within the Falcon UI before you scan. Furthermore, you can build a CIS benchmark policy based on a scan of a golden image and it automatically updates your benchmark scan to match the values found on your golden image. This is a great step up for any of you who have known the pain of struggling with Nessus .nasl and audit files.
CrowdStrike also announced some other splashy features including Attack Path Analysis and AI based remediation criticality based on Predictors of Attack. The idea is that CrowdStrike will be able to identify likely attack paths an attacker may take in your infrastructure and prioritize your vulnerability remediation based on any choke points in the various attack chains. While the concept is interesting, we are unconvinced this is a technology that you can hang your hat on. If you don’t do any type of threat modeling today, this may provide some value. However, much like the ‘Detection Posture Management’ (MITRE mapping) feature that CrowdStrike announced, we feel that this new tool may give customers a false sense of security. Our opinion is that these tools are not mature enough to identify all likely attack paths so you should consider this tool as a data point, not a dictionary.
CrowdStrike also announced that soon customers would benefit from AI that automatically can apply a criticality rating to your assets based on the hosts services and network information. This criticality rating can then be leveraged to help prioritize remediation using the ExPRT.ai (Exploit Prediction Rating). We would recommend testing this feature out to determine how accurately it maps your critical assets before leveraging it heavily in your vulnerability prioritization.
One feature that kind of flew under the radar that could have big potential is that Spotlight vulnerability data will soon be ingested by NG-SIEM. This could unlock a lot of advanced reporting options and even could provide risk correlation during investigations in Advanced Search. CrowdStrike suggested this would be available to Spotlight/Exposure management clients in the first half of 2025.
New Products
CrowdStrike not only announced enhancements to current products but they also revealed some notable new offerings. While it seems these new products may be in early stages, we did get a preview to understand some of the basic functionality.
Project Kestrel
CrowdStrike announced Project Kestrel, a new and customizable interface to interact with the Falcon platform. CrowdStrike purports that the new interface will allow a unified data experience and will help break down silos in your security and IT teams. The UI is customizable down to the individual user level so each person can view the Falcon platform how they prefer.
While this new interface may be a boon to specialized teams who need to see data in a very specific way, we were somewhat underwhelmed by the announcement. It is obviously early on in development but the screenshots that we were shown looked like little more than customizable dashboards which is already a feature within the tool. All the underlying data should also be in NG-SIEM so there are already customizable visualizations you can give to queried data. While we hope to be wrong, our early perception is that this won’t be a game changer for most teams. However, we are reserving our judgement until the product is a bit further in development. If you are curious, you can work with your account rep to sign up for early beta access.
CrowdStrike Signal
Visualization of Crowdstrike Signal event anomalies.
Our favorite new product announcement was CrowdStrike Signal. Signal leverages patented AI and ML to automatically generate threat leads by grouping detections, IOAs and events by device type. As an analogy, consider Signal as the endpoint/system equivalent of UBA (user behavior analytics) except that CrowdStrike is leveraging its vast amount of customer data to refine and fine tune what is expected behavior for a specific type of host. The initial implementation will focus only on 1st party detections and indicators of attack but is supposed to expand to other telemetry and alerts ingested to NG-SIEM from 3rd party data sources.
The goal with Signal is to reduce noise and present only truly anomalous activity. If implemented well, this could be a game changer for organizations that have to sift through dozens or hundreds of alerts per day. The initial implementations will have a built-in ‘threshold’ of what issues will be escalated via Signal but the goal is to allow you to customize your threshold through policy so that you can adjust it based on your team’s workload and risk posture. CrowdStrike reports that Signal should be available to all Falcon Insight (EDR) customers in the first half of 2025.
AI Innovations
CrowdStrike continued to tout a myriad of AI innovations throughout its product including expanding use cases for its Charlotte AI. The Charlotte AI module has some interesting functionality to summarize and build an incident report for you. Consider this similar to how ChatGPT can generate best-guess summarizations based on a given data set. CrowdStrike announced that they hope to soon release updates to Charlotte which will allow the AI to triage detections and incidents in another attempt to reduce the amount of work that is placed on the shoulders of your analysts and prioritize what is important to investigate. While this is an exciting space, Helios would recommend that you proceed with caution as AI is still in its infancy and sometimes acts like an imaginative toddler (e.g. AI hallucinations). CrowdStrike expects this new triage functionality to be available to customers with the Charlotte AI module in the first half of 2025.
CrowdStrike also announced that they are building their own internal AI engine that is purpose built for security functions. While details were sparse, this is an exciting undertaking and something that could be transformative for the platform. Our interpretation is that they are starting to slowly admit that training a non-purpose built LLM with security data doesn’t necessarily make a great security tool. While we are excited to track the progress, we expect this to be a long journey. Don’t expect any material updates on “Charlotte 2.0” for some time.
Finally, CrowdStrike announced a feature currently in beta to leverage AI to help write custom parsing scripts for data sources in NG-SIEM. The goal is to ease the learning curve on writing custom parsing logic for unique or unsupported data sources. While the technology may be welcome to those who have dealt with the headache maintaining data extraction and parsing mechanisms, like many AI solutions, you really need to understand the underlying techniques and technologies to be able to confidently leverage the generated output. Furthermore, the AI will likely not be able to account for things that require business context, like dropping noisy and superfluous logs/fields, maintaining the right balance of ingestion volume vs licensing, and normalizing data with the other logging formats you use within your organization. While we plan to track this feature, we remind folks of the hype curve that we are seeing across all purported new AI tech.
Final Thoughts
After three long days in the desert, we remain excited about the direction and overall potential of the CrowdStrike platform. It is clear that they are not resting on their laurels and are continuing to innovate on all their modules (maybe save Falcon Mobile). While we can’t pretend that this summer’s '“Crowd-stroke” event was just a bad dream, we came away from the conference remaining steadfast that CrowdStrike is a platform Helios will continue to recommend, support, and manage for our clients. If you are ready to upgrade your security platform or are otherwise looking to maximize your current investment in CrowdStrike, we would be happy to help. Contact us today to so that we can develop a support model that works for your business.